
- Data Comm & Networks Home
- DCN - Overview
- DCN - What is Computer Network
- DCN - Uses of Computer Network
- DCN - Computer Network Types
- DCN - Network LAN Technologies
- DCN - Computer Network Models
- DCN - Computer Network Security
- DCN - Components
- DCN - Connectors
- DCN - Switches
- DCN - Repeaters
- DCN - Gateways
- DCN - Bridges
- DCN - Socket
- DCN - Network Interface Card
- DCN - NIC: Pros and Cons
- DCN - Network Hardware
- DCN - Network Port
- Computer Network Topologies
- DCN - Computer Network Topologies
- DCN - Point-to-point Topology
- DCN - Bus Topology
- DCN - Star Topology
- DCN - Ring Topology
- DCN - Mesh Topology
- DCN - Tree Topology
- DCN - Hybrid Topology
- Physical Layer
- DCN - Physical Layer Introduction
- DCN - Digital Transmission
- DCN - Analog Transmission
- DCN - Transmission media
- DCN - Wireless Transmission
- DCN - Transmission Impairments
- DCN - Multiplexing
- DCN - Network Switching
- Data Link Layer
- DCN - Data Link Layer Introduction
- DCN - Data Link Control & Protocols
- DCN - RMON
- DCN - Token Ring Network
- DCN - Hamming Code
- DCN - Byte Stuffing
- DCN - Channel Allocation
- DCN - MAC Address
- DCN - Cyclic Redundancy Checks
- DCN - Error Control
- DCN - Flow Control
- DCN - Framing
- DCN - Error Detection & Correction
- DCN - Error Correcting Codes
- DCN - Parity Bits
- Network Layer
- DCN - Network Layer Introduction
- DCN - Network Addressing
- DCN - Routing
- DCN - Internetworking
- DCN - Network Layer Protocols
- DCN - Routing Information Protocol
- DCN - Border Gateway Protocol
- DCN - OSPF Protocol
- DCN - Network Address Translation
- DCN - Network Address Translation Types
- Transport Layer
- DCN - Transport Layer Introduction
- DCN - Transmission Control Protocol
- DCN - User Datagram Protocol
- DCN - Congestion Control
- DCN - TCP Service Model
- DCN - TLS Handshake
- DCN - TCP Vs. UDP
- Application Layer
- DCN - Application Layer Introduction
- DCN - Client-Server Model
- DCN - Application Protocols
- DCN - Network Services
- DCN - Virtual Private Network
- DCN - Load Shedding
- DCN - Optimality Principle
- DCN - Service Primitives
- DCN - Services of Network Security
- DCN - Hypertext Transfer Protocol
- DCN - File Transfer Protocol
- DCN - Secure Socket Layer
- Network Protocols
- DCN - ALOHA Protocol
- DCN - Pure ALOHA Protocol
- DCN - Sliding Window Protocol
- DCN - Stop and Wait Protocol
- DCN - Link State Routing
- DCN - Link State Routing Protocol
- Network Algorithms
- DCN - Shortest Path Algorithm
- DCN - Routing Algorithm
- DCN - Leaky Bucket Algorithm
- Wireless Networks
- DCN - Wireless Networks
- DCN - Wireless LANs
- DCN - Wireless LAN & IEEE 802.11
- DCN - IEEE 802.11 Wireless LAN Standards
- DCN - IEEE 802.11 Networks
- Multiplexing
- DCN - Multiplexing & Its Types
- DCN - Time Division Multiplexing
- DCN - Synchronous TDM
- DCN - Asynchronous TDM
- DCN - Synchronous Vs. Asynchronous TDM
- DCN - Frequency Division Multiplexing
- DCN - TDM Vs. FDM
- DCN - Code Division Multiplexing
- DCN - Wavelength Division Multiplexing
- Miscellaneous
- DCN - Shortest Path Routing
- DCN - B-ISDN Reference Model
- DCN - Design Issues For Layers
- DCN - Selective-repeat ARQ
- DCN - Flooding
- DCN - E-Mail Format
- DCN - Cryptography
- DCN - Unicast, Broadcast, & Multicast
- DCN - Network Virtualization
- DCN - Flow Vs. Congestion Control
- DCN - Asynchronous Transfer Mode
- DCN - ATM Networks
- DCN - Synchronous Vs. Asynchronous Transmission
- DCN - Network Attacks
- DCN - WiMax
- DCN - Buffering
- DCN - Authentication
- DCN Useful Resources
- DCN - Quick Guide
- DCN - Useful Resources
Link State Routing Protocol in Computer Networks
Link State Routing Protocol
In the Link - State Routing Protocol, the router attempts to construct its own internal map of the network topology. It provides the information about whether the link to reach the router is active or not.
Every router will create something called Link state packets.
In the first round every node creates link state packets with the help of Hello packets.
Step 2
Step 1 Prepare the link state packet at every router.
| D | |
| Seq | |
| TTL | |
| C | 11 |
| B | 7 |
| A | 1 |
| C | |
| Seq | |
| TTL | |
| D | 11 |
| B | 3 |
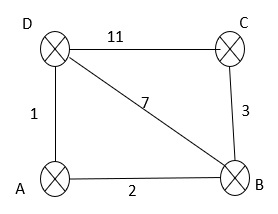
| A | |
| Seq | |
| TTL | |
| B | 2 |
| D | 1 |
| B | |
| Seq | |
| TTL | |
| A | 2 |
| D | 7 |
| C | 3 |
Step 2 Every router flood the link state packets to every offer router
At A
Link state packet B, C, D
From B
| A | 2 |
| C | 3 |
| D | 7 |
From C
| B | 3 |
| D | 11 |
From D
| A | 1 |
| B | 7 |
| C | 11 |
Now A can construct the entire graph using the received link protocol.
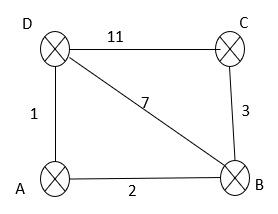
Like this, every node is able to construct the graph in its own memory. Every node has an entire graph. So every router can apply the Dijkstra algorithm to find the shortest path.
Advantages
The advantages of link-state routing protocol are as follows
-
Fast Network Convergence: It is the main advantage of the link-state routing protocol. Because of receiving an LSP, link-state routing protocols immediately flood the LSP out of all interfaces without any changes except for the interface from which the LSP was received.
-
Topological Map: Link-state routing uses a topological map or SPF tree for creating the network topology. Using the SPF tree, each router can separately determine the shortest path to every network.
-
Hierarchical Design: Link-state routing protocols use multiple areas and create a hierarchical design to network areas. The multiple areas allow better route summarization.
-
Event-driven Updates: After initial flooding of LSPs, the LSPs are sent only when there is a change in the topology and contain only the information regarding that change. The LSP contains only the information about the affected link. The link-state never sends periodic updates.
Disadvantages
The disadvantages of link-state routing protocol are as follows
-
Memory Requirements The link-state routing protocol creates and maintains a database and SPF tree. The database and SPF tree required more memory than a distance vector protocol.
-
Processing Requirements Link-state routing protocols also require more CPU processing because the SPF algorithm requires more CPU time than distance-vector algorithms just like Bellman-Ford because link-state protocols build a complete map of the topology.
-
Bandwidth Requirements The link-state routing protocol floods link-state packet during initial start-up and also at the event like network breakdown, and network topology changes, which affect the available bandwidth on a network. If the network is not stable it also creates issues on the bandwidth of the network.