
- Data Comm & Networks Home
- DCN - Overview
- DCN - What is Computer Network
- DCN - Uses of Computer Network
- DCN - Computer Network Types
- DCN - Network LAN Technologies
- DCN - Computer Network Models
- DCN - Computer Network Security
- DCN - Components
- DCN - Connectors
- DCN - Switches
- DCN - Repeaters
- DCN - Gateways
- DCN - Bridges
- DCN - Socket
- DCN - Network Interface Card
- DCN - NIC: Pros and Cons
- DCN - Network Hardware
- DCN - Network Port
- Computer Network Topologies
- DCN - Computer Network Topologies
- DCN - Point-to-point Topology
- DCN - Bus Topology
- DCN - Star Topology
- DCN - Ring Topology
- DCN - Mesh Topology
- DCN - Tree Topology
- DCN - Hybrid Topology
- Physical Layer
- DCN - Physical Layer Introduction
- DCN - Digital Transmission
- DCN - Analog Transmission
- DCN - Transmission media
- DCN - Wireless Transmission
- DCN - Transmission Impairments
- DCN - Multiplexing
- DCN - Network Switching
- Data Link Layer
- DCN - Data Link Layer Introduction
- DCN - Data Link Control & Protocols
- DCN - RMON
- DCN - Token Ring Network
- DCN - Hamming Code
- DCN - Byte Stuffing
- DCN - Channel Allocation
- DCN - MAC Address
- DCN - Cyclic Redundancy Checks
- DCN - Error Control
- DCN - Flow Control
- DCN - Framing
- DCN - Error Detection & Correction
- DCN - Error Correcting Codes
- DCN - Parity Bits
- Network Layer
- DCN - Network Layer Introduction
- DCN - Network Addressing
- DCN - Routing
- DCN - Internetworking
- DCN - Network Layer Protocols
- DCN - Routing Information Protocol
- DCN - Border Gateway Protocol
- DCN - OSPF Protocol
- DCN - Network Address Translation
- DCN - Network Address Translation Types
- Transport Layer
- DCN - Transport Layer Introduction
- DCN - Transmission Control Protocol
- DCN - User Datagram Protocol
- DCN - Congestion Control
- DCN - TCP Service Model
- DCN - TLS Handshake
- DCN - TCP Vs. UDP
- Application Layer
- DCN - Application Layer Introduction
- DCN - Client-Server Model
- DCN - Application Protocols
- DCN - Network Services
- DCN - Virtual Private Network
- DCN - Load Shedding
- DCN - Optimality Principle
- DCN - Service Primitives
- DCN - Services of Network Security
- DCN - Hypertext Transfer Protocol
- DCN - File Transfer Protocol
- DCN - Secure Socket Layer
- Network Protocols
- DCN - ALOHA Protocol
- DCN - Pure ALOHA Protocol
- DCN - Sliding Window Protocol
- DCN - Stop and Wait Protocol
- DCN - Link State Routing
- DCN - Link State Routing Protocol
- Network Algorithms
- DCN - Shortest Path Algorithm
- DCN - Routing Algorithm
- DCN - Leaky Bucket Algorithm
- Wireless Networks
- DCN - Wireless Networks
- DCN - Wireless LANs
- DCN - Wireless LAN & IEEE 802.11
- DCN - IEEE 802.11 Wireless LAN Standards
- DCN - IEEE 802.11 Networks
- Multiplexing
- DCN - Multiplexing & Its Types
- DCN - Time Division Multiplexing
- DCN - Synchronous TDM
- DCN - Asynchronous TDM
- DCN - Synchronous Vs. Asynchronous TDM
- DCN - Frequency Division Multiplexing
- DCN - TDM Vs. FDM
- DCN - Code Division Multiplexing
- DCN - Wavelength Division Multiplexing
- Miscellaneous
- DCN - Shortest Path Routing
- DCN - B-ISDN Reference Model
- DCN - Design Issues For Layers
- DCN - Selective-repeat ARQ
- DCN - Flooding
- DCN - E-Mail Format
- DCN - Cryptography
- DCN - Unicast, Broadcast, & Multicast
- DCN - Network Virtualization
- DCN - Flow Vs. Congestion Control
- DCN - Asynchronous Transfer Mode
- DCN - ATM Networks
- DCN - Synchronous Vs. Asynchronous Transmission
- DCN - Network Attacks
- DCN - WiMax
- DCN - Buffering
- DCN - Authentication
- DCN Useful Resources
- DCN - Quick Guide
- DCN - Useful Resources
Types of Network Address Translation (NAT)
Network Address Translation (NAT) is used to convert a private IP address into a public IP address and also a public IP address into private IP address. We use NAT due to the shortage of IP addresses.
IP Version 4 is a 32- bit address and it has almost 4.3 billion IP addresses, but the population of the world is much higher and it is approximately 7.8 billion as of the latest reports of June 2020.
Most of them use multiple gadgets and devices like smartphones, laptops, tablets, and many more for accessing the internet for various needs. All these devices need an IP address.
So, 4.3 billion of IP addresses is not sufficient for more than 7.8 billion of people using , that is the reason why we are using NAT. NAT is used to convert a private IP address onto public and public IP address into private.
Types of NAT
The types of Network Address Translation (NAT) are explained below
Static NAT
It is otherwise called balanced NAT. In this sort of NAT, just the IP addresses and the header checksum are changed among the general organization addresses.
These are actualized for interconnection of two particular IP networks having contrary tending to.
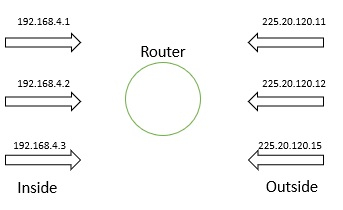
STATIC NAT is ONE to ONE NAT. This means in the local area network side and outside network side we need an equal number of IP addresses to translate. Due to that reason this is a bit expensive because we need more Public IP addresses.
Keep in mind Public IP addresses are always expensive. In this example 192.168.4.1 always translates to 225.20.120.11.
The diagram given below is for the Static NAT
Dynamic NAT
In this kind of NAT, planning of IP from an unregistered private organization is finished with the single IP address of the enrolled network from the class of enlisted IP addresses.
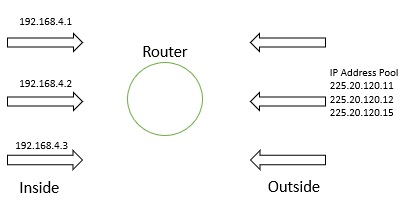
Dynamic NAT means we have a Pool of IP addresses in the outside list. So which IP addresses are Free in the outside list which will associate to LAN side IP first.
This example 192.168.4.1 from Local will check which Public IP address is from the pool.
If First IP free then it translates to First IP. If the first IP is already associated with any other local side IP, it will check the next available IP.
Suppose there is no IP available from the Public IP pool for translating Private IP addresses. Then, that traffic will drop by Router or Firewall.
The diagram given below depicts Dynamic NAT
Overloading NAT
It is additionally a sort of Dynamic NAT which is likewise alluded to as one-to-numerous NAT.
In this sort of NAT, the bundles going in the organization from the private organization to a public organization implies the Internet will have a modification in the source address of the information parcel.
Moreover, when the parcels are returned from the public organization to the private organization they will have an adjustment in the objective IP addresses.
Overlapping NAT
Sometimes in a systems administration framework, the enlisted IPs utilized by the inward organization are likewise being used by another organization and are enrolled IP's of that organization.
Consequently, for this situation, the switch keeps a query table with itself so it can catch such cases and can trade them with the extraordinary, enrolled IP addresses.